Vimana Diaries: Recon Flights in Python CGI landscapes - part II
Exception-Driven Recon: Expanding Your Attack Surface
Building upon our initial findings, we now focus on a more structured analysis of exceptions within Python web applications. Our research has identified two main scenarios: passive exceptions without user manipulation, and active exceptions induced through targeted fuzzing of URL parameters. Understanding these categories is crucial, as they form the basis for more sophisticated reconnaissance tactics.
With this foundation, we can better classify and define the exceptions based on their behavior, triggers, and the type of information they can potentially expose. This section will provide a deeper dive into these concepts, offering a clearer framework for recognizing, categorizing, and exploiting exceptions effectively.
Categories of Exceptions
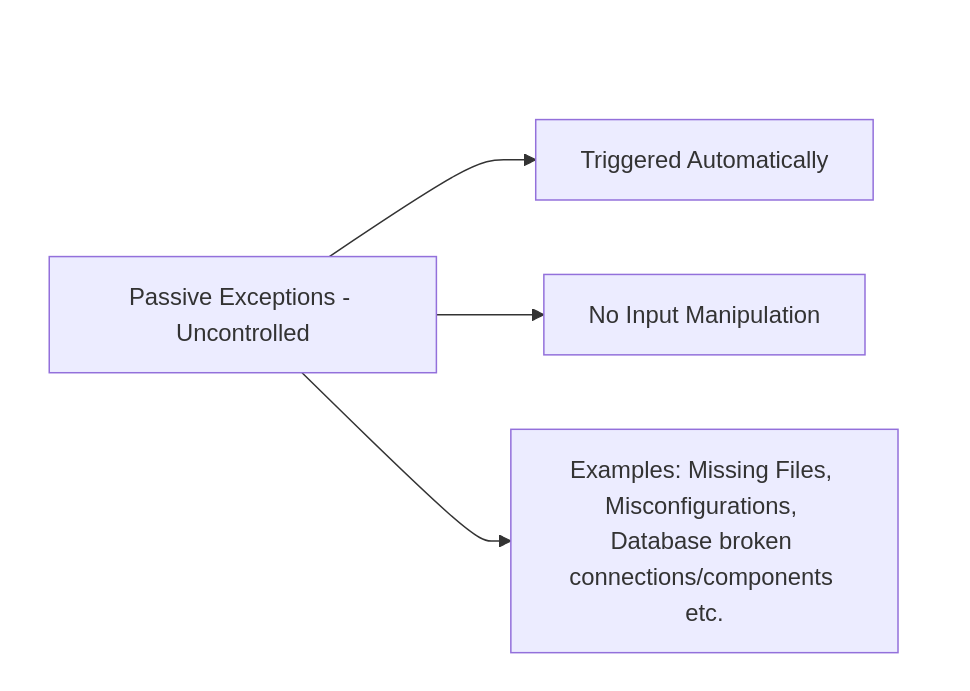
A. Passive Exceptions (Uncontrolled)
These exceptions are triggered automatically when visiting an application URL without any external input manipulation. The exception is caused by the application's internal logic, configuration errors, or unforeseen code paths that are already present in the code.
Characteristics:
No direct control or manipulation from the attacker.
Triggered immediately upon accessing the URL.
Often exposes critical internal details such as stack traces, environment variables, and application states.
Examples:
Main causes:
Missing files or resources (FileNotFoundError).
Misconfigurations causing ImportError or ModuleNotFoundError.
Syntax or logic errors (SyntaxError, TypeError).
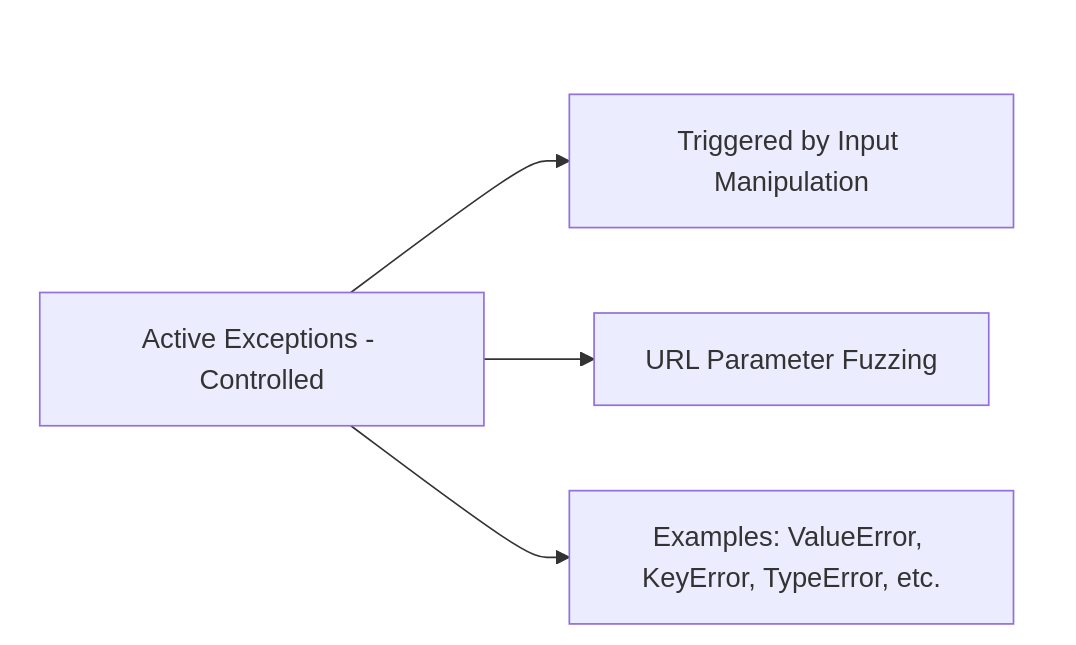
B. Active Exceptions (Controlled)
Exceptions intentionally triggered by an attacker manipulating or fuzzing URL parameters. The goal is to break the normal application flow and induce errors that might expose sensitive information.
Characteristics:
Requires active input manipulation, such as sending unexpected data types, special characters, or SQL-like inputs.
Can be fine-tuned based on the application's responses to specific inputs.
Often provides opportunities for deeper insights into the application's handling of errors, potentially revealing sensitive data or exploitable paths.
Examples:
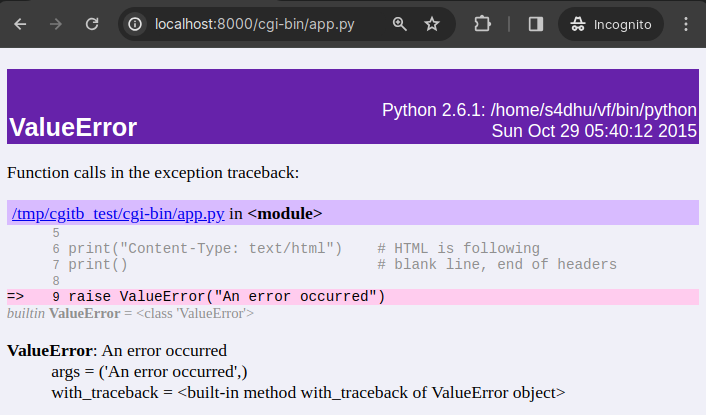
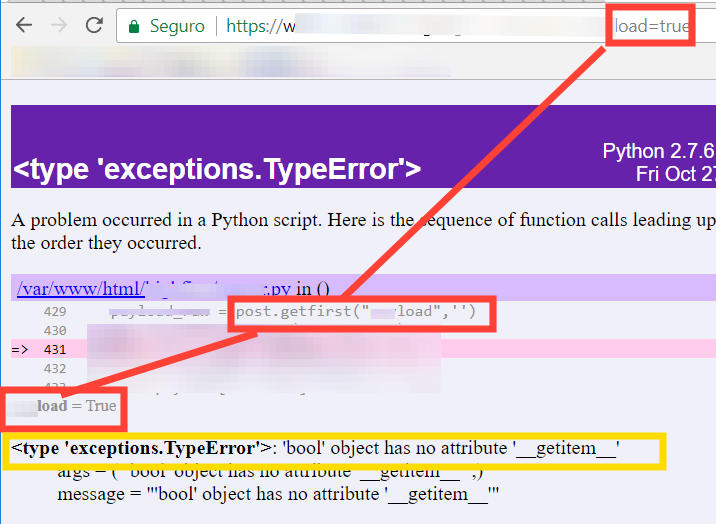
Triggering a TypeError: bool object has no attribute ‘__getitem__’ by manipulating a GET parameter with ‘true’ which becomes True and breaks the logic that expects a dict key:
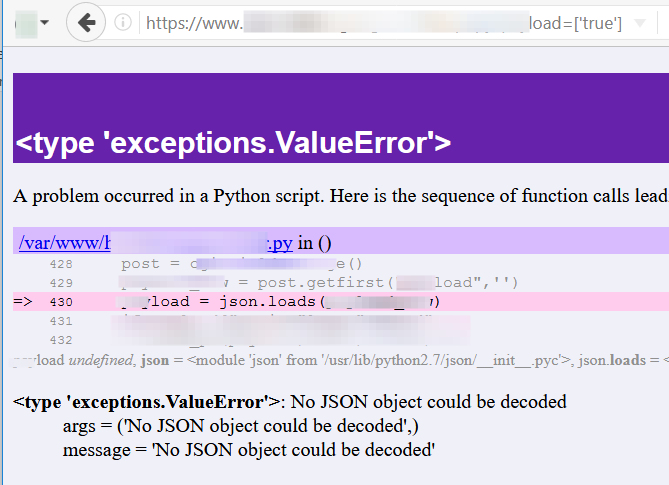
Here we trigger a different exception class, ValueError by using [‘true’] in the parameter:
Common Triggers:
Using a string where an integer is expected, causing a ValueError.
Submitting an invalid dictionary key, resulting in a KeyError.
Overloading inputs to create OverflowError or other boundary-related exceptions.
Types of Exceptions (Based on Exploitation Potential)
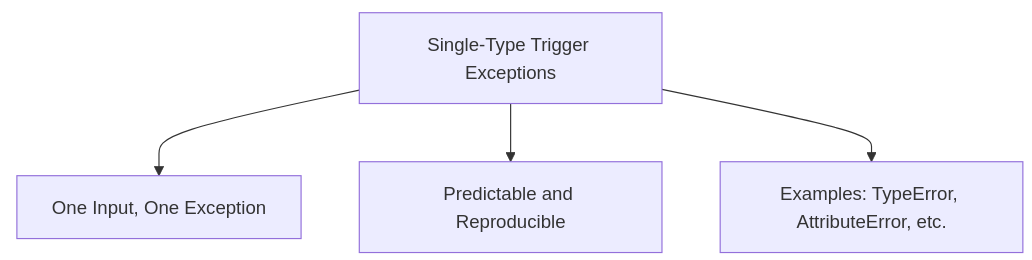
A. Single-Type Trigger Exceptions
Exceptions that occur when a parameter or input triggers a specific, single exception due to a mismatch or an error in processing:
Characteristics:
One input causes one type of exception.
Easier to predict and replicate.
Usually indicates a single point of failure or vulnerability.
Examples:
Passing 1.2 instead of 1 where an integer is expected, triggering a TypeError ('float' object has no attribute '__getitem__').
Using None in a place where a function expects a string, causing an AttributeError.
Passing two values in the same parameter causing an UnboundLocalError Exception
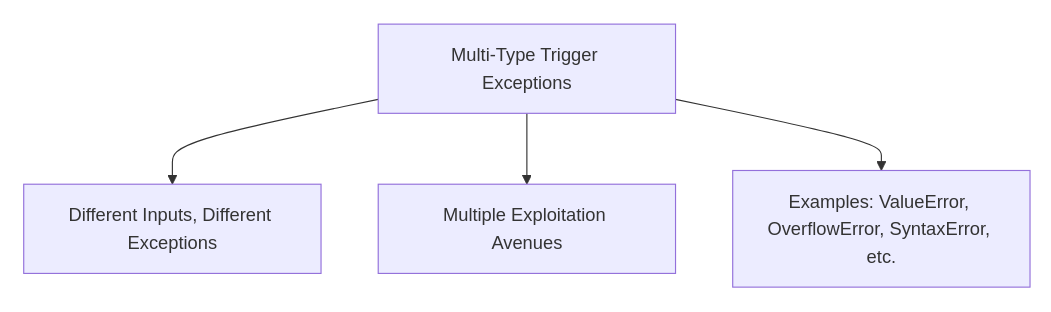
B. Multi-Type Trigger Exceptions
Exceptions that result when fuzzing the same parameter causes different types of exceptions depending on the nature of the input:
Characteristics:
Different inputs to the same parameter can produce a variety of exceptions, providing multiple avenues for exploitation.
Indicative of deeper logic flaws or insufficient input validation.
Can reveal more detailed information about the application's internal logic and data handling practices.
Examples:
Below we have a case where we can trigger the same exception class but with different values as a consequence of different causes:
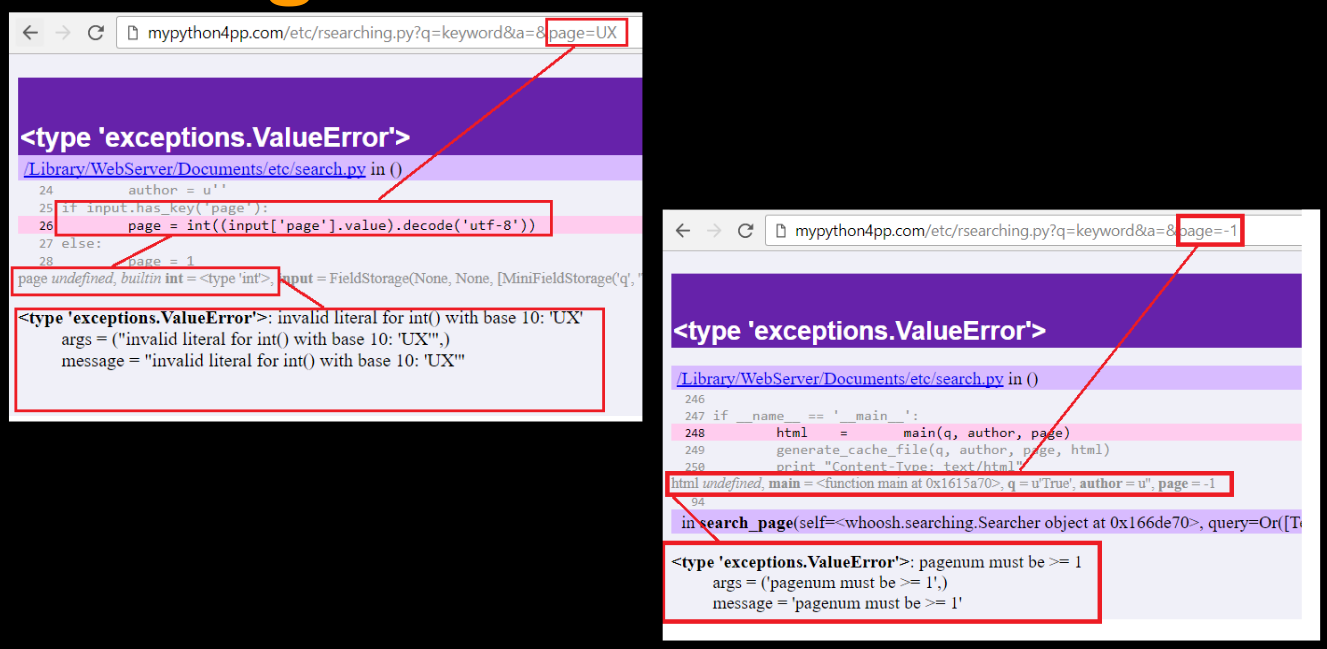
"invalid literal for int() with base 10: 'UX'"
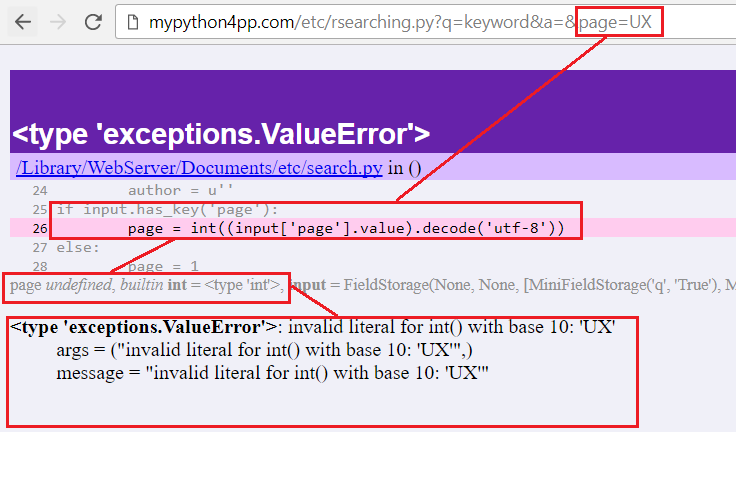
"pagenum must be >= 1"
Now, even though on the surface nothing changed since we didn’t even change the exception class, let’s look closely at each screenshot again, first the ValueError "invalid literal for int() with base 10: 'UX'" which can also be translated in terms of its root cause: “Conversion Type Error ValueError“1:
And here, following the same logic we can call it “Business logic enforcement ValueError”:
In the first one, we have the traceback showing the code snippet of search.py from 24 to 28, and in the second we have a completely different flow in the same module from lines directly into the main from lines 246 to 250, and with that, it makes it a dynamic Active Exception from this research standpoint: it flows2.
Common Triggers:
Submitting 1, 1.2, -1, and @ to a parameter that expects a specific format, potentially triggering exceptions like ValueError, TypeError, OverflowError, and SyntaxError.
Providing excessively large inputs or special characters to test for buffer overflows, injection points, or logic errors.
Information Leakage from Exceptions
A. Direct Data Exposure
Exceptions that cause the application to reveal sensitive information directly in the traceback or error message:
Characteristics:
Sensitive information is exposed as a result of the application's response to the exception.
Information might include API keys, database credentials, file paths, or other configuration data.
Critical from an exploitation perspective as it can directly aid in further attacks.
Examples:
An unhandled exception exposes a database connection string in the error message.
A traceback showing detailed file paths or user environment variables.
B. Indirect Data Exposure
Exceptions that do not directly expose sensitive information but provide clues or insights that can be used in combination with other techniques to infer or deduce sensitive data:
Characteristics:
Requires additional steps or knowledge to leverage the information gained from the exception.
May reveal non-sensitive but useful metadata, such as application versions, internal logic paths, or response patterns.
Examples:
A KeyError indicating the use of specific dictionary keys, hinting at internal data structures.
A TypeError revealing that a specific function expects a particular type, suggesting the nature of the data being processed.
Exploring Python web applications through exception handling has revealed valuable insights into how exceptions can be leveraged to gain a deeper understanding of the underlying systems. By classifying exceptions into passive and active categories, we laid the groundwork for a structured approach to reconnaissance. This analysis will not only improve defensive practices but also expose potential vulnerabilities that attackers could exploit.
With this foundational knowledge, we now turn our attention to more advanced techniques aimed at actively manipulating exceptions to uncover deeper security flaws.
Part III: Exception Manipulation Tactics: Probing for Insights and Potential Paths
*Footnotes
First Scenario: Invalid Literal for Int Conversion
Error: "invalid literal for int() with base 10: 'UX'"
Cause: The script attempts to convert a GET parameter (page=UX) to an integer. The parameter value "UX" is a string that cannot be converted to an integer, leading to a ValueError.
Code Context: The error occurs when the code tries to enforce a type conversion using int() on the page parameter which is expected to be numeric.
Potential Fix: Validate the page parameter to ensure it contains only numeric data before attempting conversion. Utilizing try-except blocks or pre-validation could prevent this error.
Second Scenario: Validation Logic Error
Error: "pagenum must be >= 1"
Cause: The script checks if the page parameter is less than 1 (i.e., page=-1). The business logic dictates that page numbers should start from 1, so passing -1 triggers a ValueError designed to enforce this rule.
Code Context: This happens during a logic check where the page number is validated against business rules specifying that pages must be numbered starting from 1. It’s a custom error message intended to notify about the improper use of the function or method.
Potential Fix: Ensure user input adheres to the expected range before it is processed. This could involve client-side validation to catch errors early and reduce server-side overhead.
→ Note: The ability to trigger various conditions that reveal different portions of the module's source code introduces a critical concept for this research: the potential for partial reconstruction of the application's source code from an attacker's perspective.
This approach aligns with a methodology I refer to as MAST (Mixed Application Security Testing) within the framework's development. By leveraging black-box testing techniques to induce and capture these code fragments, we can facilitate more thorough white-box static analysis, blending both testing approaches to gain deeper insights into the application's security posture